Deploy ExternalDNS on TCE and integrate with a Microsoft DNS server
Update 2022-10-21: After just one year in the wild VMware announced on Oct 21 2022 that they would no longer update or maintain the TCE project and that by end of 2022 the Github project will be removed. For more information check out my blog post here
Most of the things mentioned in this post (outside of installing TCE) should still be valid for other Kubernetes distributions
Following up on my multiple blog posts on installing packages through the Tanzu Package repository on Tanzu Community Edition (TCE) Kubernetes clusters we'll now take a look at external-dns.
Take a look at these blog posts to check out more about TCE and Tanzu packages
ExternalDNS can synchronize Kubernetes Services and Ingresses with external DNS providers. Note that there are a bunch of external providers that's in Alpha state, meaning they're not tested by the maintainers and come with no support.
So as always: USE AT OWN RISK, and TEST before putting anything in production.
Keep track of the status here
DNS Provider
In this example we'll work with Microsoft DNS which I'm running in my lab. A lot of this stuff is taken from Cormac Hogan's blog post which originally was created for working with a Tanzu Kubernetes Grid (TKG) cluster. For TCE and the new Tanzu package repository there are some slight differences.
There isn't a specific provider for Microsoft DNS, but we can use the RFC2136 provider to integrate.
A caveat here is that we need to work with Insecure updates
Tanzu package and configuration
In the Tanzu cluster we'll work with I've already added the Tanzu package repository, and I've deployed MetalLB for providing Load balancer services, and Contour for providing ingress functionality
So, let's check out the Tanzu package for ExternalDNS
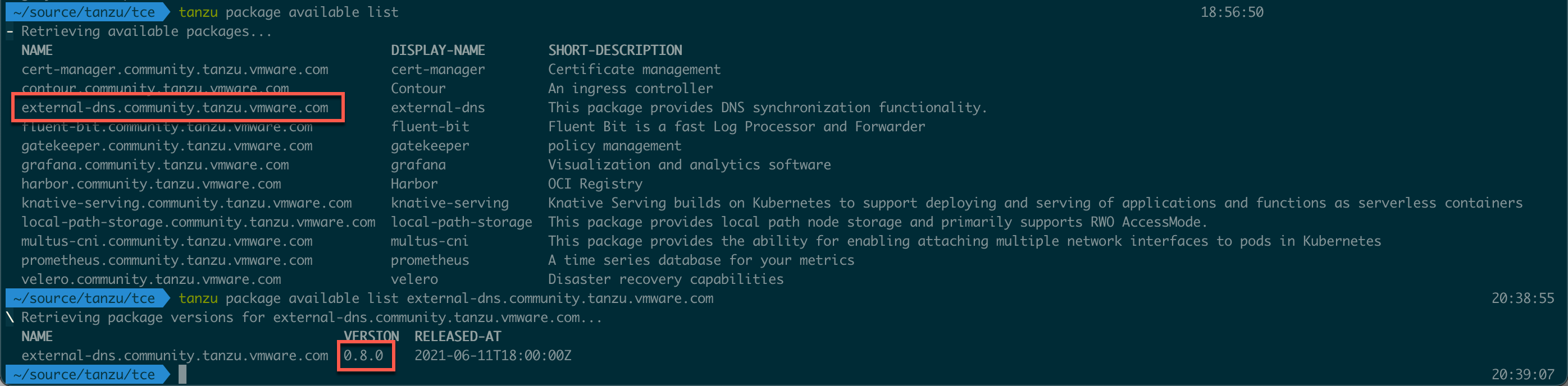
1tanzu package available list
2tanzu package available list external-dns.community.tanzu.vmware.com
Let's also retrieve the values available for the package.
1tanzu package available get external-dns.community.tanzu.vmware.com/0.8.0 --values-schema
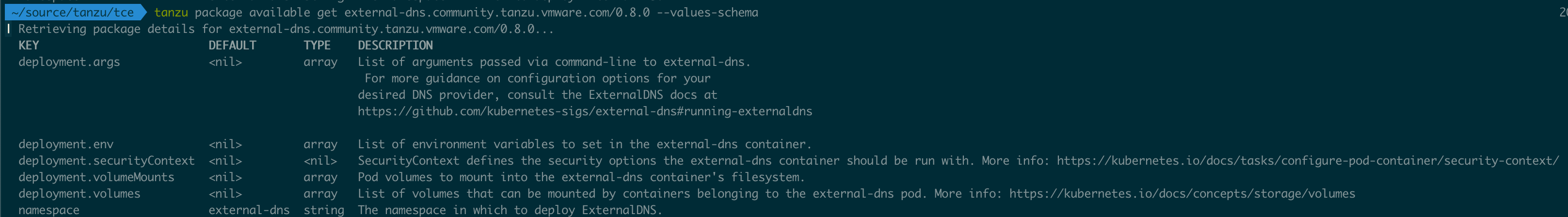
Now, those values accepts quite a few arguments. A brief description of them can be found here. For more details take a look at this Github page which discusses the options for RFC2136
Configuring the MS DNS provider
Before we look at the finalized configuration for our example we'll take a look at how I've set up my DNS server.
First of, I have a DNS server authoritative for a domain, rhmlab.local. The DNS zone is AD integrated.
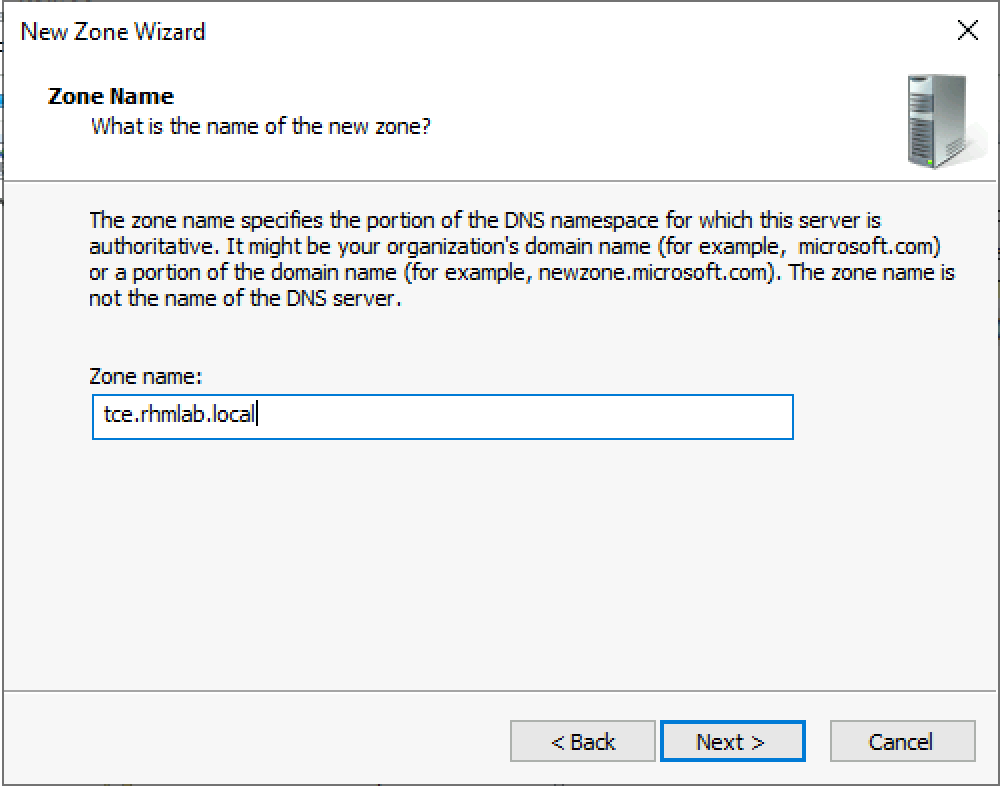
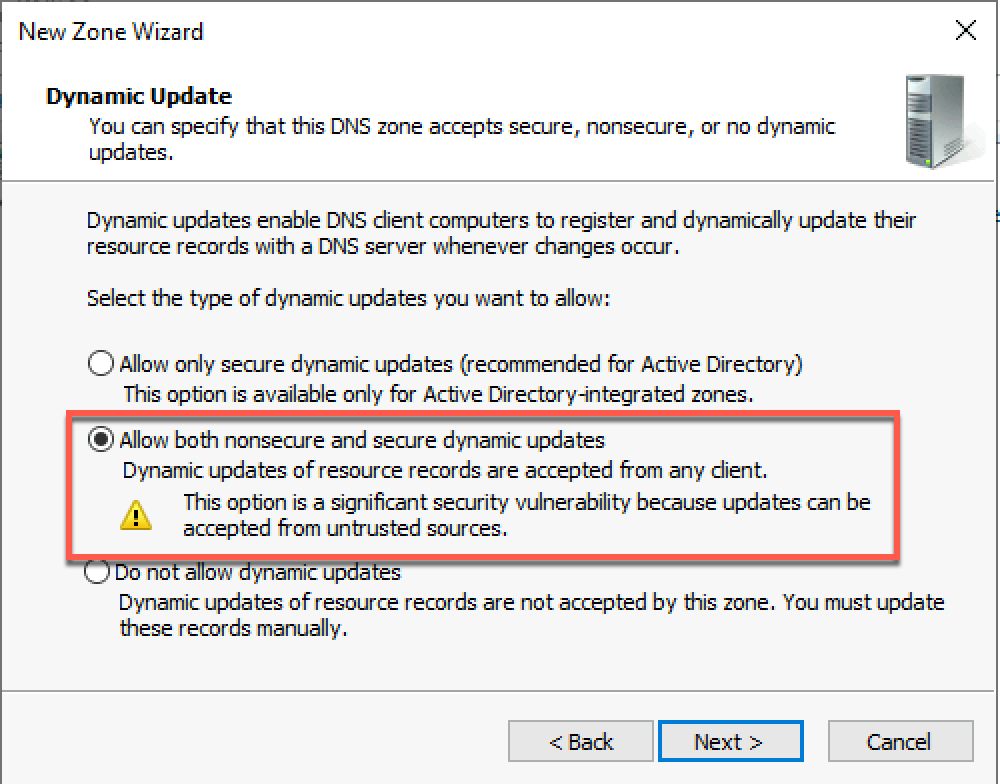
On the DNS server we'll add a new primary zone, tce.rhmlab.local, although we could have worked with the current domain as well.
Set the correct name
And as mentioned, we need to set it to allow both secure and unsecure updates
With this in place we can go ahead and create our ExternalDNS config file.
Note that the documentation specifies that we also need to allow Zone transfers to All servers. In my setup I haven't had to set this
ExternalDNS config
There's a few things we need to be sure to have in our config for ExternalDNS. Cormac describes a lot of these in his post here. We're using txt registry to avoid duplicate names. I'm not 100% sure if this is needed when I'm using a specific DNS zone, but I'll add it anyways.
To point to our DNS server and the zone we'll configure the rfc2136-host and rfc2136-zone respectively. Note also the rfc2136-insecure argument. The source arguments specifies that we're working with contour and ingress, and we finally have a domain-filter pointing to the zone name.
1namespace: external-dns
2deployment:
3 args:
4 - --registry=txt
5 - --txt-prefix=external-dns-
6 - --txt-owner-id=tanzu
7 - --provider=rfc2136
8 - --rfc2136-host=192.168.x.x
9 - --rfc2136-port=53
10 - --rfc2136-zone=tce.rhmlab.local
11 - --rfc2136-insecure
12 - --rfc2136-tsig-axfr
13 - --source=service
14 - --source=contour-httpproxy
15 - --source=ingress
16 - --domain-filter=tce.rhmlab.local
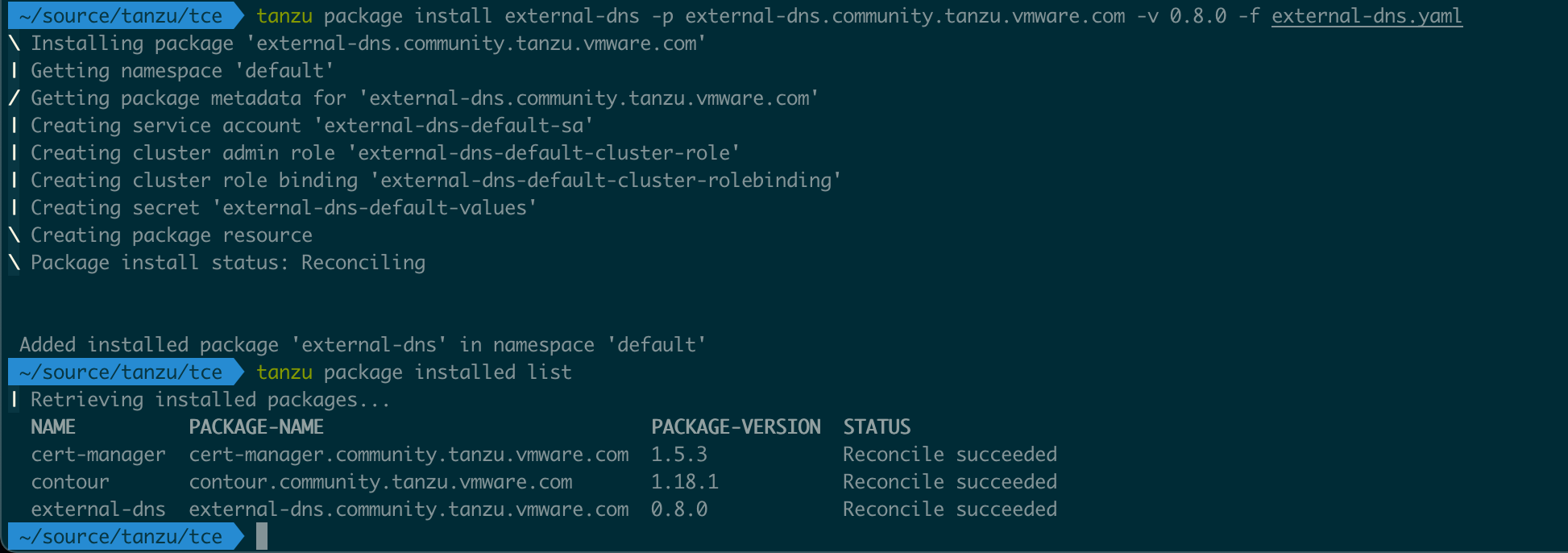
Now, let's deploy ExternalDNS! We'll point to our file with the config, and after the deployment we'll verify that the package has been reconciled
1tanzu package install external-dns -p external-dns.community.tanzu.vmware.com -v 0.8.0 -f external-dns.yaml
2tanzu package installed list
Verify ExternalDNS
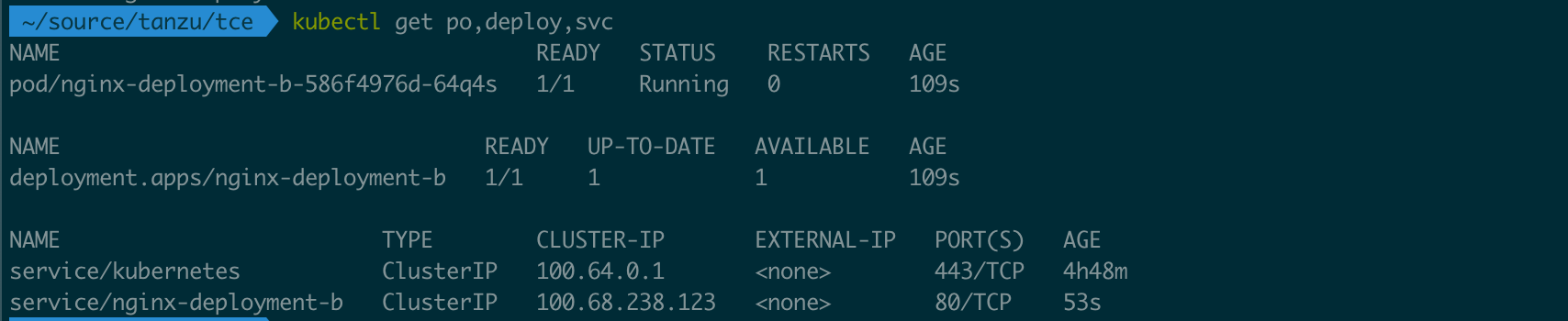
To test the ExternalDNS functionality we'll take a look at a simple nginx server that runs a custom index.html
The nginx deployment is exposed through a service of type ClusterIP
1kubectl get po,deploy,svc
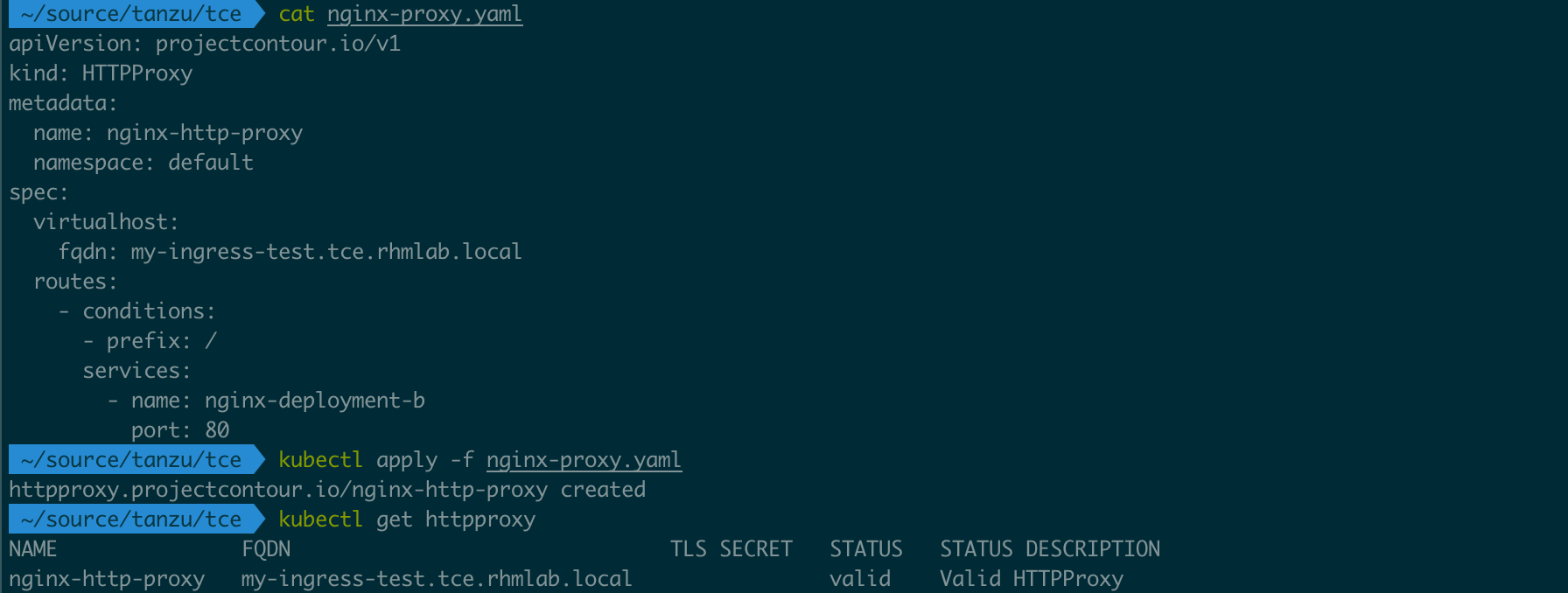
Now, we'll add a Contour HTTPProxy that points to this service and we'll set a specifc fqdn for it in the DNS domain we've created
1kubectl apply -f nginx-proxy.yaml
2kubectl get httpproxy
So let's check the DNS server
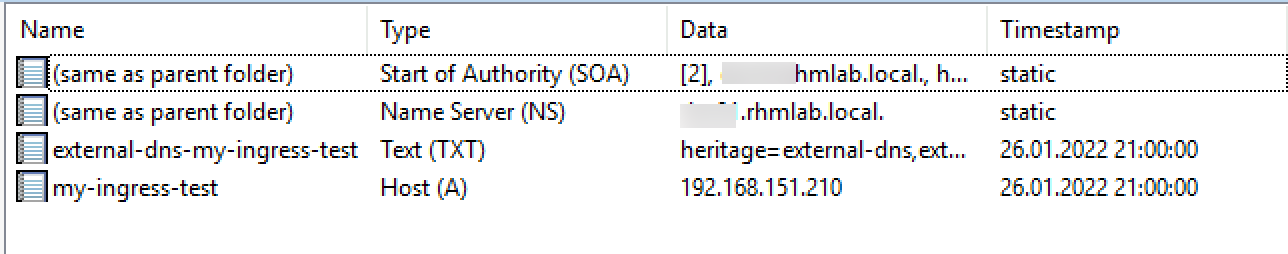
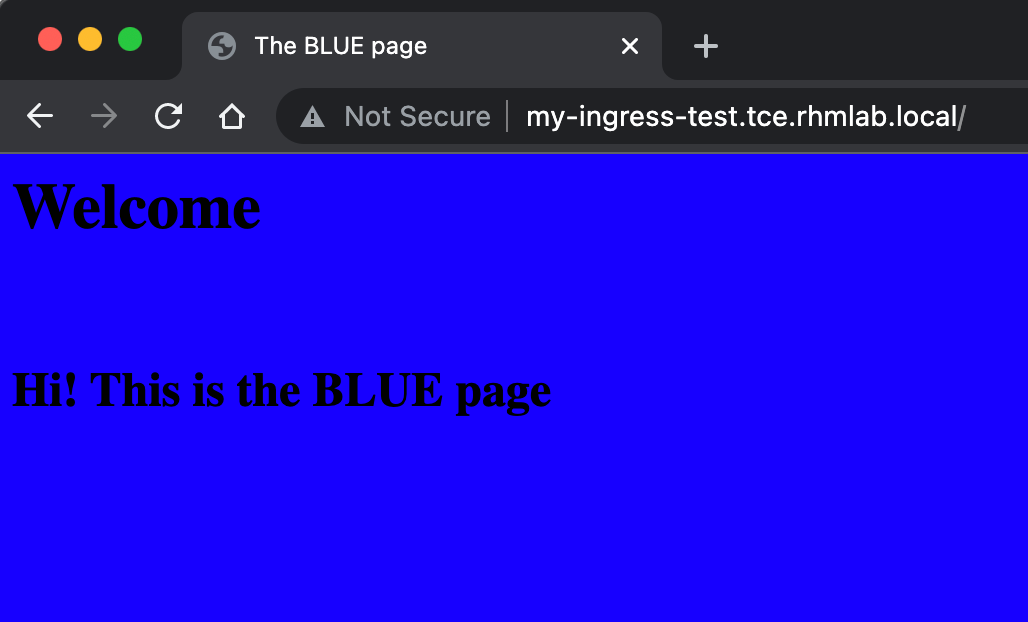
And, of course, we'll test the fqdn in a browser
Summary
This post have shown how we can deploy ExternalDNS in our TCE Kubernetes cluster which allows us to create and update DNS records in our External DNS server.
Again, note that the support for different providers is still not production like so be sure to test this out before integrating with a production DNS server, and specially if you're integrating with an existing DNS zone
Thanks for reading and please reach out if you have any questions or comments