Automate disabling of IPMI over LAN access on HPE iLO
This article will describe how you can disable the IPMI over LAN access on HPE iLO.
The IPMI protocol can present a security vulnerability where the authentication process for IPMI requires a server to send a hash of a user password to the client before authentication. This is not a new vulnerability and since this is a part of the specification of the protocol there is no fix for it besides disabling it or accepting it.
Note that iLO versions 2, 3 and 4 have the IPMI over LAN access enabled by default whereas iLO version 5 has disabled this by default.
If you need the functionality you should try to mitigate potential risks by isolating the iLO network, use strong passwords that are changed regularly etc. If you have verified that you don't need the functionality HPE recommends to disable it.
You have a few options for disabling the IPMI setting:
iLO Web GUI:
- In the iLO web interface go to Administration -> Access Settings
- Change the IPMI/DCMI over LAN Access to "Disabled"
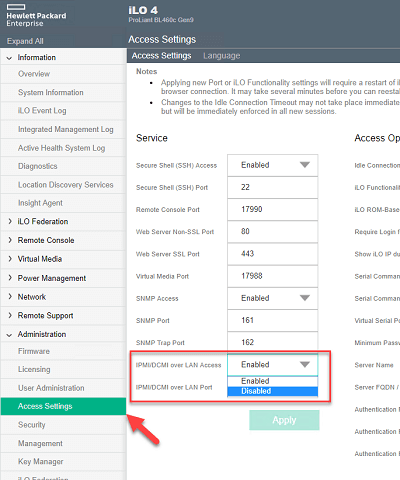
Disable IPMI
Scripting:
If you have a lot of servers you probably want to automate/script this.
It seems that the only method to change this setting programatically is through a RIBCL script. The RIBCL scripting functionality is a way to change settings through an upload of an XML file to the iLO. There are a few options for passing this script to a server. For example you can use the HPQLOCFG utility, the HPONCFG utility or the HPE Powershell cmdlets. The following HPE PDF specifies usage of the different tools to script against iLO, however it does not cover the Powershell module.
Both the HPQLOCFG utility and the PS cmdlets can be installed on a server and if you have access to the iLO you can pass in the following xml to the command:
<RIBCL VERSION="2.0">
<LOGIN USER_LOGIN="admin" PASSWORD="password">
<RIB_INFO MODE="write">
<MOD_GLOBAL_SETTINGS>
<IPMI_DCMI_OVER_LAN_ENABLED VALUE="No"/>
</MOD_GLOBAL_SETTINGS>
</RIB_INFO>
</LOGIN>
</RIBCL>
Note that in a RIBCL script you can either specify the login credentials in the xml or when you run the command. The latter will overwrite what's in the script.
HPQLOCFG:
The hpqlocfg syntax is as follows:
hpqlocfg.exe -s "serveraddress" -f "your RIBCL script" -u "username" -p "password" -n (specifies no logging, use -l and a path to a logfile if you want a file output)
Note that you need to pass the username and password to the command if you haven't specified it in your script. The command will not prompt you for the information.
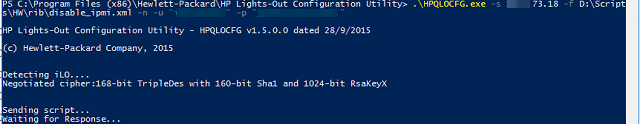
HPQLOCFG command
Powershell:
In this example we are utilizing the Invoke-HPiLORIBCLCommand cmdlet from the HPiLO module
First we're loading the RIBCL script from a file to a variable (you could also paste the script in directly) and then using this variable as the RICLCommand
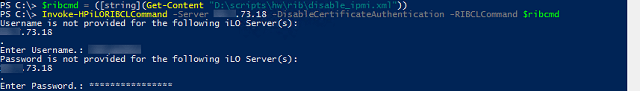
HPONCFG via Powershell
HPONCFG:
If you have Proliant server blades you can also utilize the Onboard Administrator CLI and run the hponcfg utility directly to the server blades:
The procedure for passing a RIBCL script to the hponcfg on OA is:
- Type "hponcfg", a space and then the specific blade number(s) you want to run against, or "all" for all blades, then a new space
- Type "<<" followed by a space
- Type a string that does not appear in the RIBCL, this will be used to signalize when the script is finished (end marker). I've used "EOF" as the end marker
- Press ENTER for a new line
- Paste in your RIBCL script
- Press ENTER for a new line
- Type your end marker
- Press ENTER to run the command
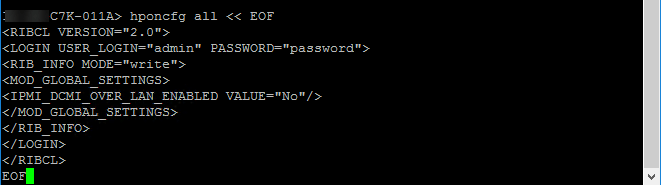
HPONCFG on OA
The hponcfg command will run the RIBCL script against the specified blades and will output it's result.