CKA Study notes - Pod Service Account
Overview
This post is part of my Certified Kubernetes Administrator exam preparations. In this post we'll take a quick look at how to specify which service account a Pod should use when communicating with the API server. I think for the CKA (and CKAD) exam the most important thing to know is how to specify a service account, but I'm covering a bit more.
Update January 2024: This post was written in 2021 preparing for the CKA on version 1.19. An updated post for version 1.28 can be found here
Service accounts can be used for giving a Pod access to specific resources through the API server just as a user working through the kubectl can. They can also be assigned imagePullSecrets which gives them access to pull container images from private repositories.
Note #1: I'm using documentation for version 1.19 in my references below as this is the version used in the current (jan 2021) CKA exam. Please check the version applicable to your usecase and/or environment
Note #2: This is a post covering my study notes preparing for the CKA exam and reflects my understanding of the topic, and what I have focused on during my preparations.
Service accounts for Pods
Kubernetes Documentation reference
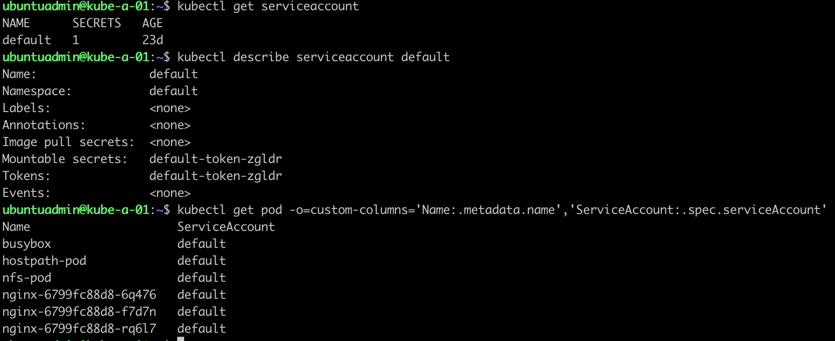
By default every pod uses the Default service account (for the namespace) when it's communicating with the api-server. We can verify this by checking this in my namespace here
1kubectl get serviceccount
2kubectl describe serviceaccount default
3
4kubectl get pod -o=custom-columns='Name:.metadata.name','ServiceAccount:.spec.serviceAccount'
Create service account
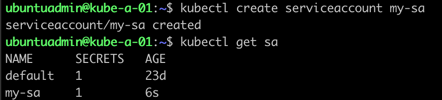
Let's create a simple service account
1kubectl create serviceaccount <sa-name>
2kubectl get sa
Assign service account to pod
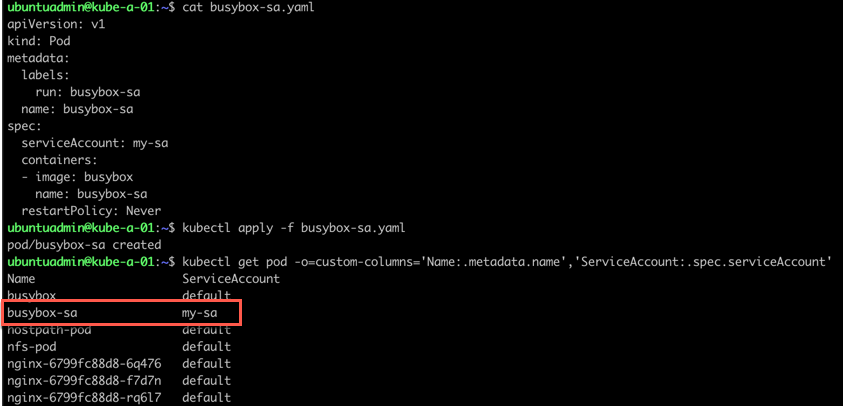
Now let's create a yaml manifest for a Pod and specify the serviceaccount
1apiVersion: v1
2kind: Pod
3metadata:
4 labels:
5 key: value
6 name: <name>
7spec:
8 serviceAccount: <sa-name>
9 containers:
10 - image: <image>
11 name: <name>
12 restartPolicy: Never
Assign imagePullSecrets
Now let's try to run a Pod with an image on my private Docker hub account.
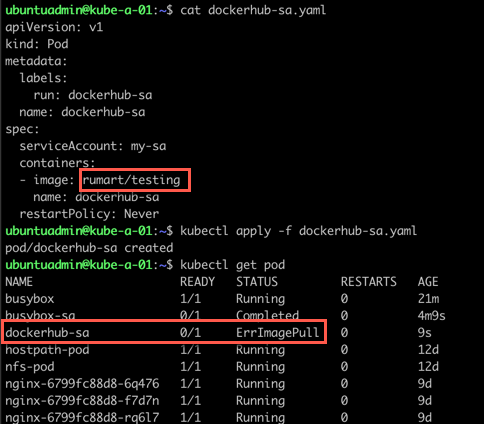
Let's add some Docker hub credentials to the service account and try again. The Kubernetes documentation has a reference to how you can add a secret with your Docker hub credentials
With this I've created a secret with my personal credentials for accessing my private Docker hub registry
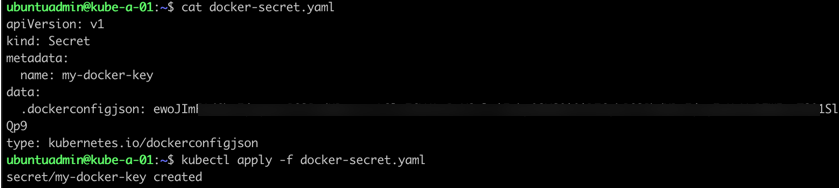
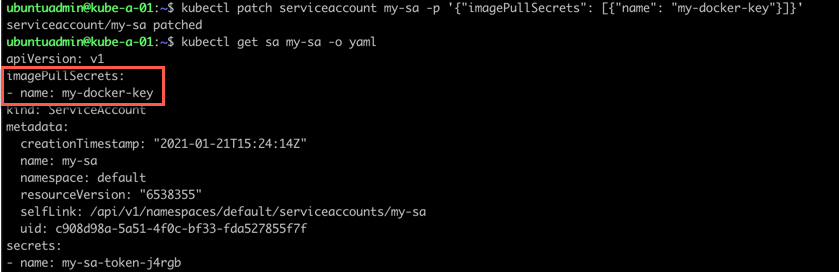
Now, I'll add this to the imagePullSecrets of my new service account (reference)
1kubectl patch serviceaccount <sa-name> -p '{"imagePullSecrets": [{"name": "<key>"}]}'
After this I'll delete and recreate my Pod and then the image can be pulled successfully
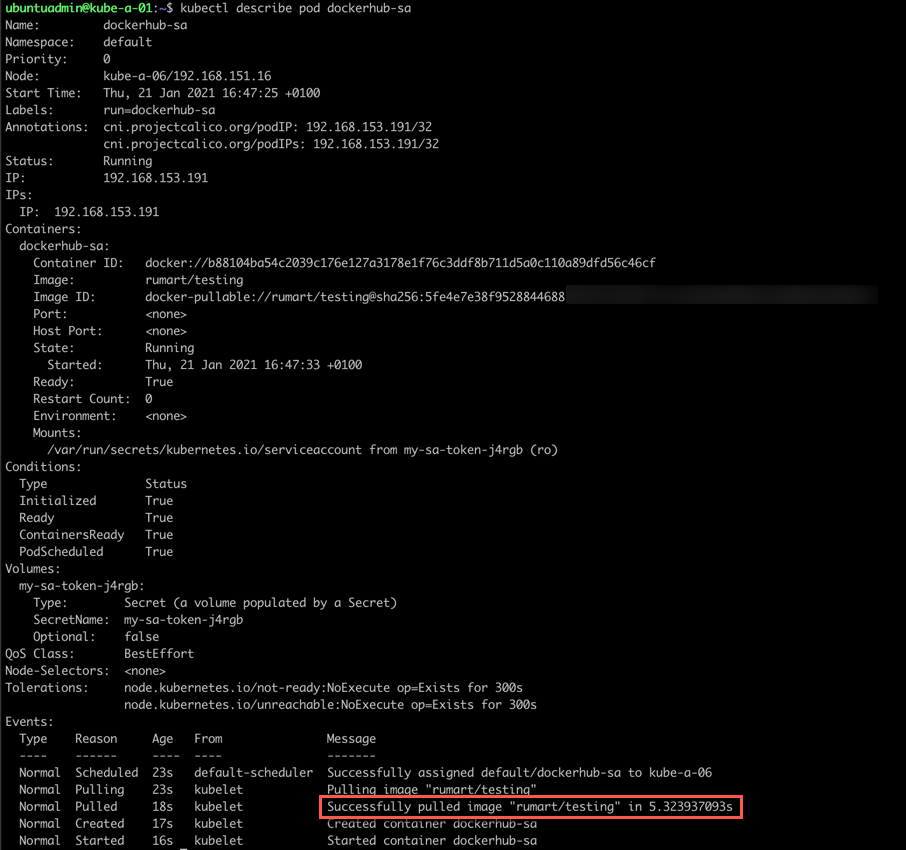
Note that imagePullSecrets can be assigned directly to a Pod as well, but then you'd have to add that to each Pod spec
Service account permissions
Kubernetes Documentation reference
Service accounts can be assigned permissions in the cluster and in other namespaces which let's you be pretty specific in what your service accounts are allowed to and not.
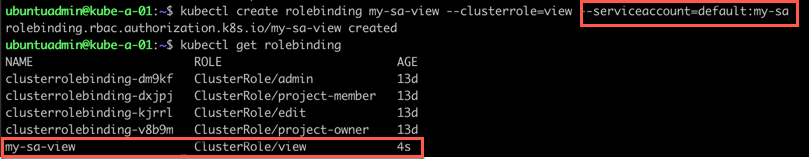
Normally this is done by creating a Role binding which binds a role to a service account
1kubectl create rolebinding <role-bind-name> --role=<role-name> --serviceaccount=<namespace>:<sa-name> --namespace=<namespace>
Summary
This has been a short intro to service accounts in Kubernetes and how to assign it to a Pod. There's much more to service accounts, but for the CKA exam this should be enough. For more details on service accounts and pods, refer to the documentation